Blog
Are your email practices HIPAA compliant? A checklist for healthcare

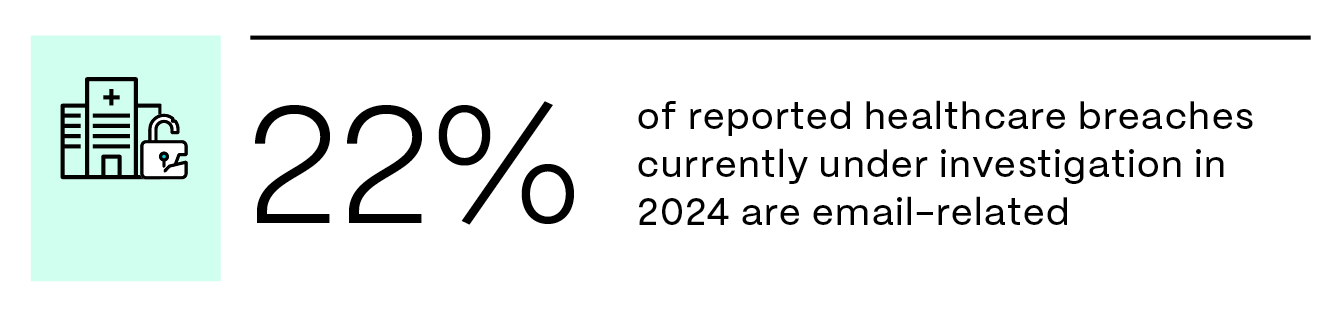
Email is a critical communication tool for healthcare providers, but it also poses significant risks when handling sensitive data. Approximately one in five reported healthcare breaches under investigation in 2024 is email-related.
Ensuring HIPAA (Health Insurance Portability and Accountability Act) compliance in your email practices is essential for protecting patient privacy, building trust, and avoiding legal consequences.
Whether you're setting up a new email system or reviewing your current framework, this guide can help you implement the right protocols to meet HIPAA’s secure email requirements.

Key takeaways
- HIPAA’s purpose is to protect sensitive patient data, such as medical records and billing details, from unauthorized access and breaches.
- There are three main HIPAA email security requirements: encryption, access controls, and audit trails.
- A checklist can be followed for optimizing email server security, from training employees to performing regular risk assessments.
- It’s important to focus on solutions that offer the necessary features to meet HIPAA standards, such as a signed business associate agreement.
A brief refresh on HIPPA and its importance
Enacted in 1996, HIPAA is a federal law designed to protect the privacy and security of individuals' health information. Its primary goal is to safeguard personal patient data, known as PHI (protected health information), from unauthorized access and breaches. PHI includes any information that can identify a person, such as medical records and billing details.
Healthcare professionals understand the importance of HIPAA, both for compliance requirements and maintaining patient trust. Failing to protect PHI can result in financial repercussions and reputational damage, so security is a top priority when handling confidential information.
Understanding HIPAA secure email requirements for compliance
Healthcare organizations must follow specific rules to maintain HIPAA and email server security. These policies are designed to prevent breaches and make sure PHI is accessible only to approved individuals.
Here are three security requirements to follow:
Encryption standards
Encryption ensures that even if an email containing PHI is intercepted, unauthorized individuals cannot access the information. This protection measure is particularly important for healthcare providers sharing PHI externally, whether with patients or other medical professionals.
Using encryption converts sensitive data into scrambled, unreadable code that only authorized recipients with the appropriate decryption key can decipher. HIPAA requires encryption of PHI to meet NIST (National Institute of Standards and Technology) standards, which includes using advanced protocols like AES (advanced encryption standard) to maintain data security.
Access controls and authentication
Access controls verify that only permitted personnel can view and send emails containing PHI, reducing the risk of unapproved access to private information.
Authentication is pivotal in this process as it confirms that the person accessing PHI via email is who they claim to be. Common strategies include 2FA (two-factor authentication) and SSO (single sign-on) solutions to provide an extra layer of protection.
Audit and monitoring requirements
Regular audits help guarantee compliance by tracking who accesses PHI and how it is used or shared. Continuous monitoring provides a critical defense method, so organizations can detect and respond to potential compromises or unpermitted access.
Additionally, healthcare organizations must maintain records of these audits as part of compliance efforts. Detailed logs of email activity can demonstrate adherence during investigations or audits by regulatory bodies.
Checklist for HIPAA and email server security compliance
You may be asking, “how do I make my email HIPAA compliant?” Use the checklist below to ensure your email practices comply with regulations and effectively safeguard both patient and company data.
1. Deploy end-to-end encryption
- Encrypt all emails containing PHI: Modify the data in emails containing PHI to make it appear random to unauthorized users.
- Confirm encryption during transit and at rest: Use encryption algorithms like TLS (transport layer security) and AES to scramble data both when it's sent (in transit) and when it's stored (at rest).
- Continuously update encryption protocols: Routinely improve your encryption practices so systems remain compliant and safe as new threats emerge.
2. Implement multi-factor authentication (MFA)
- Require MFA for all email accounts accessing PHI: Mandate users to provide two or more forms of verification as an extra layer of protection before access is granted. For example, entering a password then a one-time code sent via text.
- Set up alerts for unusual access attempts: Establish monitoring systems that notify IT teams of suspicious logins from unfamiliar devices or locations to proactively mitigate hacks.
3. Use secure email gateways and filters
- Adopt a secure email gateway (SEG): Incorporate a SEG either as a cloud service or as a local device to block harmful content from your incoming or outgoing emails.
- Implement content filters for PHI: Sift out malicious emails before they reach users with automated filters, minimizing the risk of threats like phishing, malware, and spam.
4. Make sure email servers meet HIPAA standards
- Host email on a HIPAA-compliant server: Confirm your email server is hosted by a provider that complies with HIPAA standards, including maintaining encryption, access controls, and audit capabilities.
- Conduct regular vulnerability assessments: Frequently evaluate systems and practices to uncover weaknesses in your email server’s security. This enables you to address potential threats before they escalate into breaches.
5. Maintain audit trails and logs
- Log all email activity related to PHI: Maintain in-depth logs, including emails sent, accessed, or modified, to provide a clear accountability trail.
- Consistently review logs: Monitor and review logs regularly to identify unusual behavior and support incident response efforts when necessary.
6. Train employees on HIPAA email policies
- Provide initial and ongoing training: Train all employees on email safety, particularly when new policies and protocols are introduced. Provide refresher courses quarterly, for example, to be sure everyone is compliant.
- Conduct phishing and security drills: Run phishing simulations and other security exercises to help employees recognize potential threats. This reduces the likelihood of issues due to human error.
7. Obtain a business associate agreement (BAA)
- Enter into a BAA with your email service provider: Confirm your email service is HIPAA compliant and responsible for protecting PHI with a signed BAA contract.
- Annually review BAA compliance: Perform annual renewals of the BAA to make sure your provider continues to comply with regulations and addresses any updates to security procedures.
8. Establish a data-retention and disposal policy
- Institute guidelines for retaining PHI emails: Set clear rules on how long emails should be kept or archived as HIPAA dictates specific retention periods (e.g., six years).
- Ensure emails and backups are securely disposed of: Automate the secure deletion of emails containing PHI from servers and backups once the retention period expires to comply with HIPAA’s data destruction guidelines.
9. Perform regular risk assessments
- Conduct periodic assessments: Routinely evaluate potential risks to your email system, including unapproved access and improper email practices.
- Document and act on findings: Record what your risk assessments find and take prompt action to address vulnerabilities and prevent future incidents.
10. Adopt a PHI data-loss prevention (DLP) solution
- Implement DLP for outgoing emails: Deploy DLP tools to automatically detect confidential information and prevent it from being sent without encryption or to unauthorized recipients.
- Automate alerts for potential violations: Set up automated alerts to inform your IT team of potential misconducts to allow for timely interception, such as attempts to send unencrypted emails containing PHI.
Related read:Top 16 email security best practices 2024 - a comprehensive guide
Choosing the right HIPAA-compliant email solution
Choosing a reliable email solution is crucial for healthcare organizations to avoid breaches and penalties and foster efficient communication with patients and colleagues.
With many email services available, it’s important to focus on solutions that offer the necessary features and requirements to meet HIPAA standards. For example:
- Encryption: Makes all emails, attachments, and metadata indecipherable both in transit and at rest to protect PHI from unauthorized access, even if the email server is compromised.
- DLP tools: Helps prevent private information from being accidentally or intentionally shared with unapproved recipients.
- Audit logging: Assists with regulatory audits and incident response by maintaining detailed logs of all email activity, including sender, recipient, subject, and content.
- Access control: Restricts availability to PHI based on specified user roles and permissions.
- BAA compliance: Confirms that any third-party email provider will adhere to HIPAA regulations through a signed agreement.
In addition to enhancing email security, tools likeShareFile simplify compliance management by offering automated workflows, document versioning, and permission settings. Incorporating this technology into your email solution streamlines communication while maintaining full accordance with HIPAA rules.
Conclusion
Non-compliance with HIPAA can lead to severe reputational, legal, and financial consequences. Healthcare organizations must safeguard patient privacy through email by using secure solutions and robust security measures like encryption and MFA.
Remember, following HIPAA’s secure email requirements is an ongoing process that demands vigilance and regular updates. Bookmark this page as a reference guide to stay informed about email security best practices and maintain full compliance for your organization.
Related Resources
